432/67 Wednesday, December 4, 2024
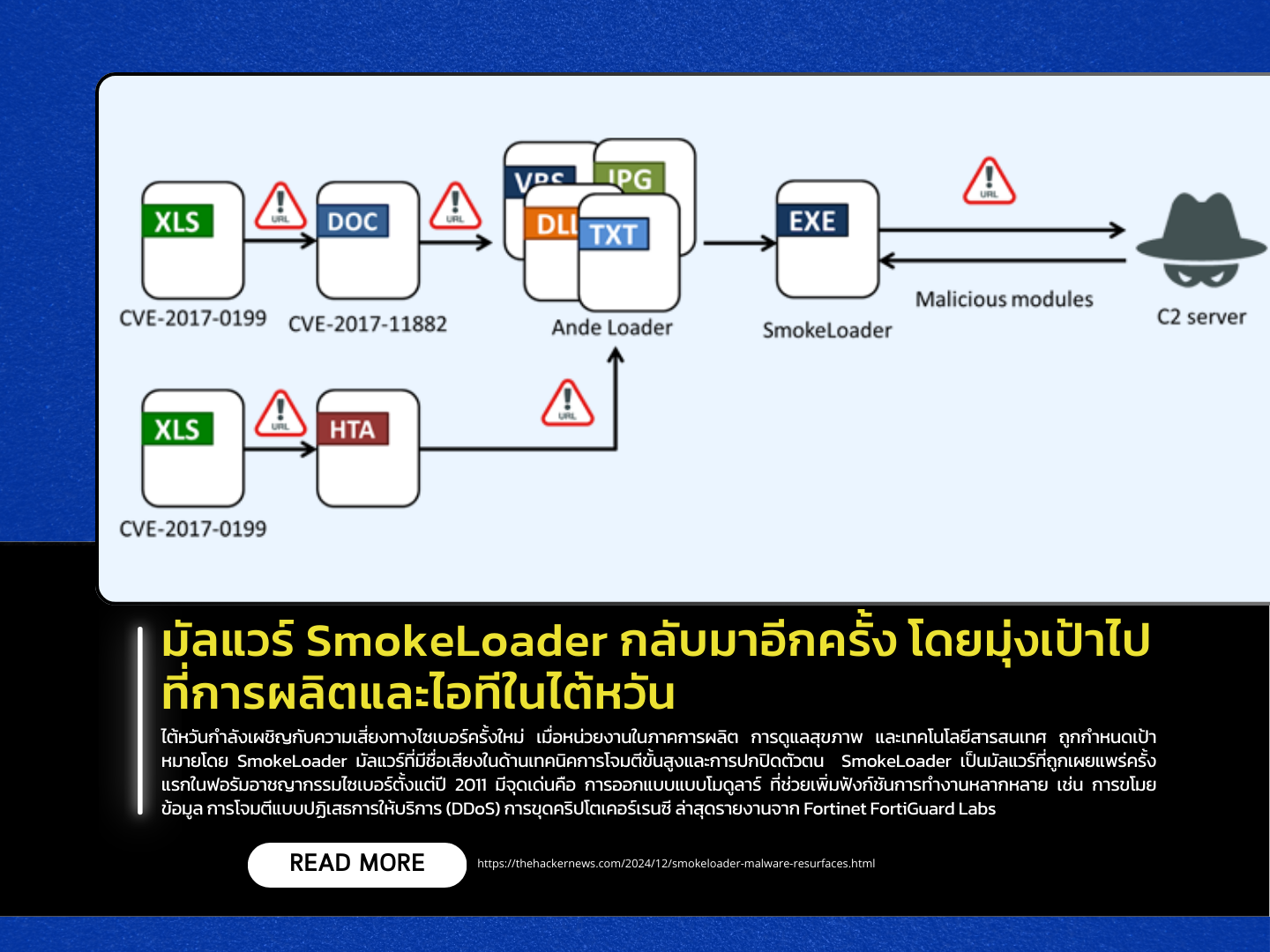
Taiwan is facing a new cybersecurity threat as organizations in the manufacturing, healthcare, and information technology sectors are being targeted by SmokeLoader, a malware notorious for its advanced attack techniques and stealth capabilities. Originally released on cybercrime forums in 2011, SmokeLoader is characterized by its modular design, which enhances its functionality for tasks such as data theft, distributed denial-of-service (DDoS) attacks, and cryptocurrency mining.
A recent report from Fortinet’s FortiGuard Labs reveals that SmokeLoader has been upgraded with enhanced evasion techniques, allowing it to establish trust within compromised systems by using plugins for operations instead of downloading full files. While SmokeLoader activity significantly declined following Europol’s Operation Endgame in May 2024—which dismantled infrastructure linked to over 1,000 malware-related domains and removed infections from over 50,000 devices—the threat has not been eradicated. Analysts from Zscaler ThreatLabz report that threat actors have rebuilt new infrastructure and distributed cracked versions of SmokeLoader online, enabling its continued use in cyberattacks.
The latest attacks uncovered by FortiGuard Labs began with phishing emails. These emails carried Microsoft Excel attachments that, when opened and activated, exploited long-standing vulnerabilities such as CVE-2017-0199 and CVE-2017-11882. This led to the installation of a malware loader known as Ande Loader, which subsequently downloaded and installed SmokeLoader.
To protect against SmokeLoader, users should avoid opening attachments in suspicious emails, keep operating systems and software updated to the latest versions, and verify the authenticity of email attachments and links before accessing them. SmokeLoader remains one of the most sophisticated and adaptive cyber threats, underscoring the importance of vigilance and adherence to cybersecurity best practices to minimize the risks associated with this malware.
Source https://thehackernews.com/2024/12/smokeloader-malware-resurfaces.html
