116/68 Tuesday, March 25, 2025
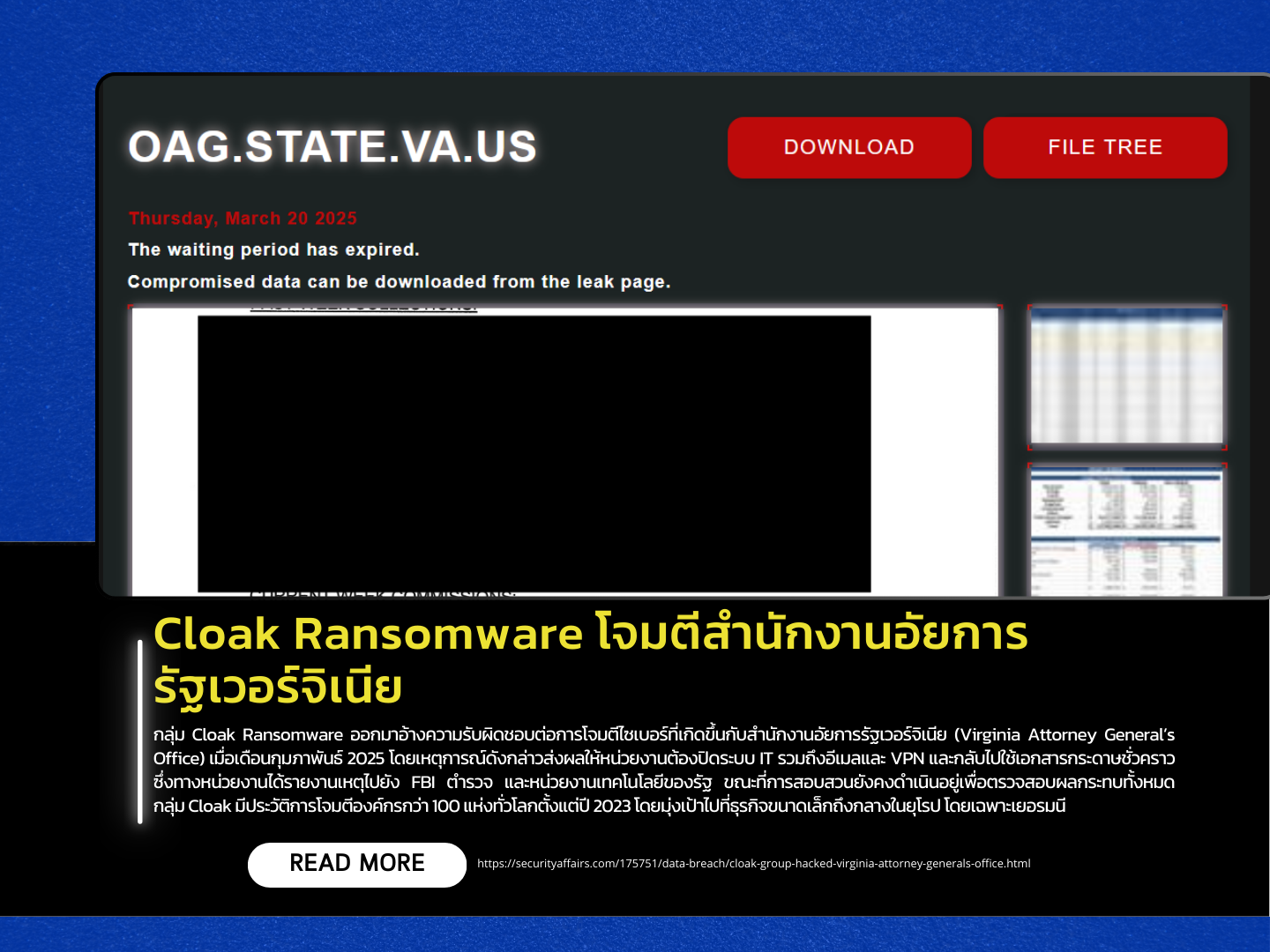
The Cloak ransomware group has claimed responsibility for a cyberattack targeting the Virginia Attorney General’s Office in February 2025. The incident forced the agency to shut down its IT systems, including email and VPN, and temporarily revert to paper-based operations. The breach was reported to the FBI, state police, and the Virginia Information Technologies Agency (VITA). Investigations are ongoing to determine the full scope and impact of the attack.
On March 20, 2025, Cloak listed the Attorney General’s Office on its Tor leak site, stating that the “waiting period is over” and claiming to have stolen 134GB of data. The group initially shared screenshots as proof, followed by releasing the entire archive for download. The attack was carried out using ARCrypter ransomware, a strain derived from the leaked source code of Babuk ransomware.
Cloak has a history of targeting over 100 organizations worldwide since 2023, primarily focusing on small to medium-sized businesses in Europe, especially in Germany, and expanding operations across Asia. The group gains access through Initial Access Brokers (IABs) and social engineering techniques such as phishing and malvertising. This incident highlights the growing threat posed by rapidly evolving cyberattacks against both public and private sector organizations.
